cybercrime costs are set
to hit $10.5 trillion
Our Lightning Platform combines breakthrough technologies including quantum-resistant encryption, proprietary cutting-edge key management, and AI-powered threat detection to deliver unmatched security capabilities.
The company’s commitment to innovation, customer success, and industry leadership positions Veekrypt as the ideal partner for organizations seeking to enhance their security posture while preparing for the challenges of tomorrow. Through comprehensive solutions, extensive resources, and dedicated support, Veekrypt enables organizations to confidently embrace digital transformation while maintaining the highest levels of security and compliance.
As cyber threats continue to evolve and quantum computing approaches practical reality, organizations need security solutions that provide both immediate protection and long-term resilience. Veekrypt’s comprehensive approach to cybersecurity ensures that customers receive the protection they need today while being prepared for the challenges of tomorrow.
Veekrypt represents the next evolution in cybersecurity, providing organizations with comprehensive protection against current and future threats while enabling secure collaboration and digital transformation.
Quality Service
Delivering future-ready cybersecurity with precision, Veekrypt ensures every client receives reliable, tailored protection against evolving threats.
Expert Team
Our team of cybersecurity innovators, CISO specialists, and AI experts drive breakthrough solutions that safeguard organizations today and tomorrow.
OUR SERVICES
Cloud Overlay Security Made Simple
Veekrypt protects your sensitive data across all platforms and cloud services,
and provides your business a solid defense against cyber attacks and data breaches.
Data Security for Cloud and Local Computer
Active Threat Defense from cyber attacks
Remote Monitoring and Management
Compliance Automation and Governance
HOW IT WORKS
Securing Your Digital Future, Step by Step
Your Challenge
Your sensitive business information, intellectual property assets and customer data are stored on your employees’ computers, mobile devices and on external cloud servers that your company uses. Securing this sensitive information is critical to protecting your business from financial risks, regulatory violations and reputation setback. How do you ensure the security of your sensitive data that is dispersed across different platforms?
Your Goal
Ensure rock-solid security for your sensitive business data regardless of wherever it is stored.
Your Challenge
Ransomware, data breaches, and cyber attacks are making headlines in the news. Several of the Fortune 500 companies, with the best-of-breed security infrastructure, have come under cyber attack which damaged their reputation and inflicted a major financial loss. Are you prepared to stop a cyber attack against your business?
Your Goal
Create a multi-layer security strategy for your business that can minimize the cyber-security risks and ensure solid protection against the ‘known’ as well as ‘unknown’ or ‘zero-day’ security threats.
Your Challenge
Your company has regional as well as global offshore offices. You have little visibility and control over what is going on in your offshore organization. Who is sharing what information? You need an ability to monitor and an effective mechanism to respond if a cyber attack or a security violation occurs.
Your Goal
Have a comprehensive remote monitoring and management solution that gives you full visibility and an effective way to respond in the face of a high severity cyber attack on any of the machines in your enterprise.
Your Challenge
In order to ensure business continuity, your business has to be compliant with certain regulations and laws that are applicable to the industries you serve and the jurisdictions in which your business operates. To ensure that your business remains compliant with those regulatory frameworks, you need trained staff, a significant compliance budget and an established process to protect your business from regulatory fines and penalties, in case a serious violation occurs and your business gets audited.
Your Goal
Have a comprehensive, cost-effective, and reasonably automated solution that ensures continuous compliance through real-time policy-driven self-healing remediation and adherence to baseline and best practices.
SECURITY SOLUTION
Cloud Security Made Simple
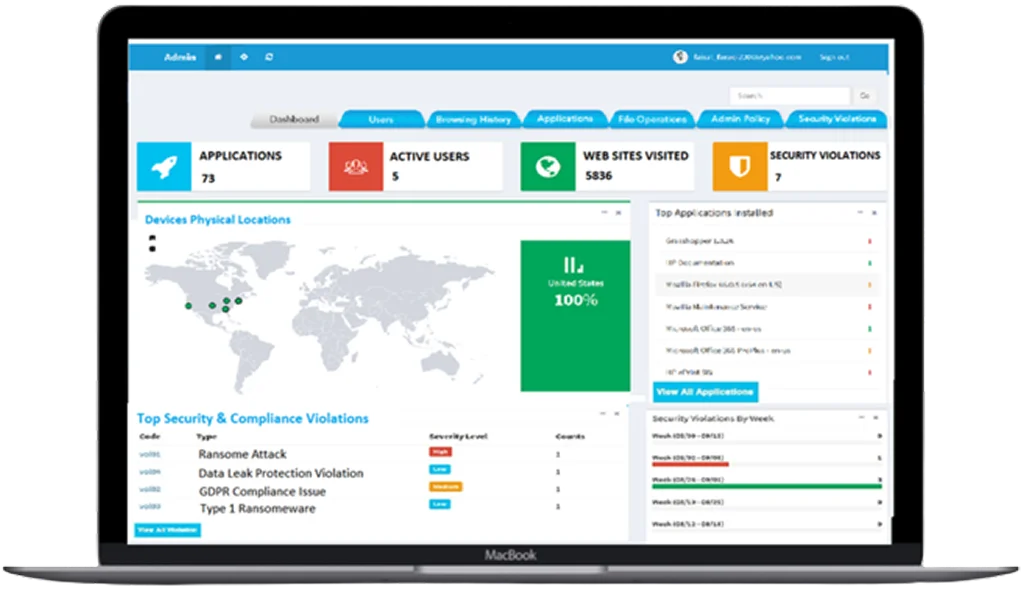
A comprehensive enterprise security solution that provides Automated Threat Detection, Global Monitoring, Data Encryption and Compliance
Automation for your business.
services
What We Offer
Data Security for Cloud, Mobile Devices and Local Computers

A comprehensive enterprise security solution that provides Automated Threat Detection, Global Monitoring, Data Encryption and Compliance Automation for your business.
Active Threat Defense from
cyber attacks

A comprehensive enterprise security solution that provides Automated Threat Detection, Global Monitoring, Data Encryption and Compliance Automation for your business.
Leverage The Power Of Cloud Overlay Encryption
Clients
Meet Our Customers








 Faisal Faruqi is a serial entrepreneur and long-time Silicon Valley veteran with over two decades of experience spanning enterprise software, mobility, and cybersecurity. He spent thirteen years at Oracle Corporation, where he contributed as one of the architects of Oracle’s flagship e-Business Suite, a platform serving millions of users worldwide. In 2010, Faisal launched his first startup in enterprise mobility, achieving notable success before devoting the past decade to pioneering research and innovation in cybersecurity. He holds a master’s degree in Computer Science and Engineering from the University of Florida. Outside of technology, Faisal is a passionate philosopher and poet, currently authoring a book that brings together his poetic works and explores his deep reflections on the human condition and the pursuit of meaning.
Faisal Faruqi is a serial entrepreneur and long-time Silicon Valley veteran with over two decades of experience spanning enterprise software, mobility, and cybersecurity. He spent thirteen years at Oracle Corporation, where he contributed as one of the architects of Oracle’s flagship e-Business Suite, a platform serving millions of users worldwide. In 2010, Faisal launched his first startup in enterprise mobility, achieving notable success before devoting the past decade to pioneering research and innovation in cybersecurity. He holds a master’s degree in Computer Science and Engineering from the University of Florida. Outside of technology, Faisal is a passionate philosopher and poet, currently authoring a book that brings together his poetic works and explores his deep reflections on the human condition and the pursuit of meaning. With over 29 years of experience in information security and compliance, Adam Nunn is a seasoned professional who has held roles as Chief Information Security Officer (CISO) and Chief Compliance Officer, focusing on the intersection of regulatory compliance and cybersecurity. Specializing in developing robust cybersecurity programs aligned with frameworks such as NIST, ISO, CIS, and HIPAA, Adam has overseen and coordinated information security initiatives for hundreds of entities across the United States and provided services worldwide, including in Europe, Asia, South America, and North America.
With over 29 years of experience in information security and compliance, Adam Nunn is a seasoned professional who has held roles as Chief Information Security Officer (CISO) and Chief Compliance Officer, focusing on the intersection of regulatory compliance and cybersecurity. Specializing in developing robust cybersecurity programs aligned with frameworks such as NIST, ISO, CIS, and HIPAA, Adam has overseen and coordinated information security initiatives for hundreds of entities across the United States and provided services worldwide, including in Europe, Asia, South America, and North America. Sujit Maharana is a seasoned technology executive with more than two decades of experience leading global engineering, cloud, and security organizations. He has served as a Chief Information Security Officer (CISO) and senior engineering leader in the SaaS industry, where he has built and scaled secure, cloud-native platforms used by millions of users worldwide.
Sujit Maharana is a seasoned technology executive with more than two decades of experience leading global engineering, cloud, and security organizations. He has served as a Chief Information Security Officer (CISO) and senior engineering leader in the SaaS industry, where he has built and scaled secure, cloud-native platforms used by millions of users worldwide.